Thanks to the increasing popularity of ecommerce platforms, many card transactions that previously would have occurred in person can now be made online. The resulting rise in card-not-present (CNP) payments offers greater convenience for those initiating the transaction and can require less from merchants, who no longer need to have a brick-and-mortar store or hire designated employees to accept payments. However, the downside to this digital modernization is that it makes instances of payment card fraud more prevalent and more difficult to stop.
Because the card and cardholder are absent from a CNP transaction, it can be difficult to verify the identity of the person making the payment and confirm its legitimacy. Whereas chip readers and PIN-pad devices can be deployed to authenticate a card-present transaction, those security measures are not available for CNP transactions. As a result, CNP transactions must use other authentication techniques during the payment process that are specific to the channel through which they are being accepted.
To reduce the risk of fraud, identity theft, and other illegitimate practices associated with these types of payments, card brands and other organizations have introduced additional authorization technologies. One such method for ensuring the authenticity of CNP payments is an authorization technique called strong customer authentication (SCA). SCA is a standard established by the EU Revised Directive on Payment Services (PSD2) that requires a form of multifactor authentication (MFA) to be used in order to successfully complete a CNP transaction.
Originally enacted in 2007 as the Payment Services Directive (PSD), the European Commission–administered PSD2 regulates payment service providers across the European Economic Area. The PSD2’s SCA control is particularly concerned with using MFA to protect customers, merchants, and banks from fraudulent transactions, and it is commonly satisfied via the use of a technology called 3-D Secure (3DS).
What is 3-D Secure Authentication?
3DS is a security protocol used to authenticate users. This provides an extra layer of protection for payment card transactions in card-not-present scenarios. It was designed to allow a cardholder to authenticate its identity to prevent payment fraud, stymie unauthorized transactions, and reduce chargebacks.
How can 3DS enhance your
payments flow?
Due to PSD2’s SCA requirement, this security protocol is used throughout Europe, but it’s also used in countries outside of the EU, such as South Africa and India. Versions of the protocol have been adopted by many card brands, including the members of EMVCo–Visa, Mastercard, Discover, American Express, JCB, and UnionPay–which spearheaded the creation of 3-D Security 2.0 (3DS2).
Components of 3-D Secure Authentication
The idea behind 3DS authentication is to provide an additional step to the financial authorization process by authenticating the cardholder. It operates according to a three-domain model, which includes:
- Acquirer domain – the environment of the acquiring bank and merchant who is receiving the payment
- Issuer domain – the environment of the issuing bank whose card is providing the payment
- Interoperability domain – the systems in place that support the 3DS process by allowing the parties in the transaction to interact and exchange information
The 3DS authentication process uses Secure Sockets Layer (SSL) protocol to send Extensible Markup Language (XML) messages with client authentication, providing digital certificates to confirm the identity of all parties involved in the transaction. This ensures maximum security.
How 3-D Secure 2.0 Works
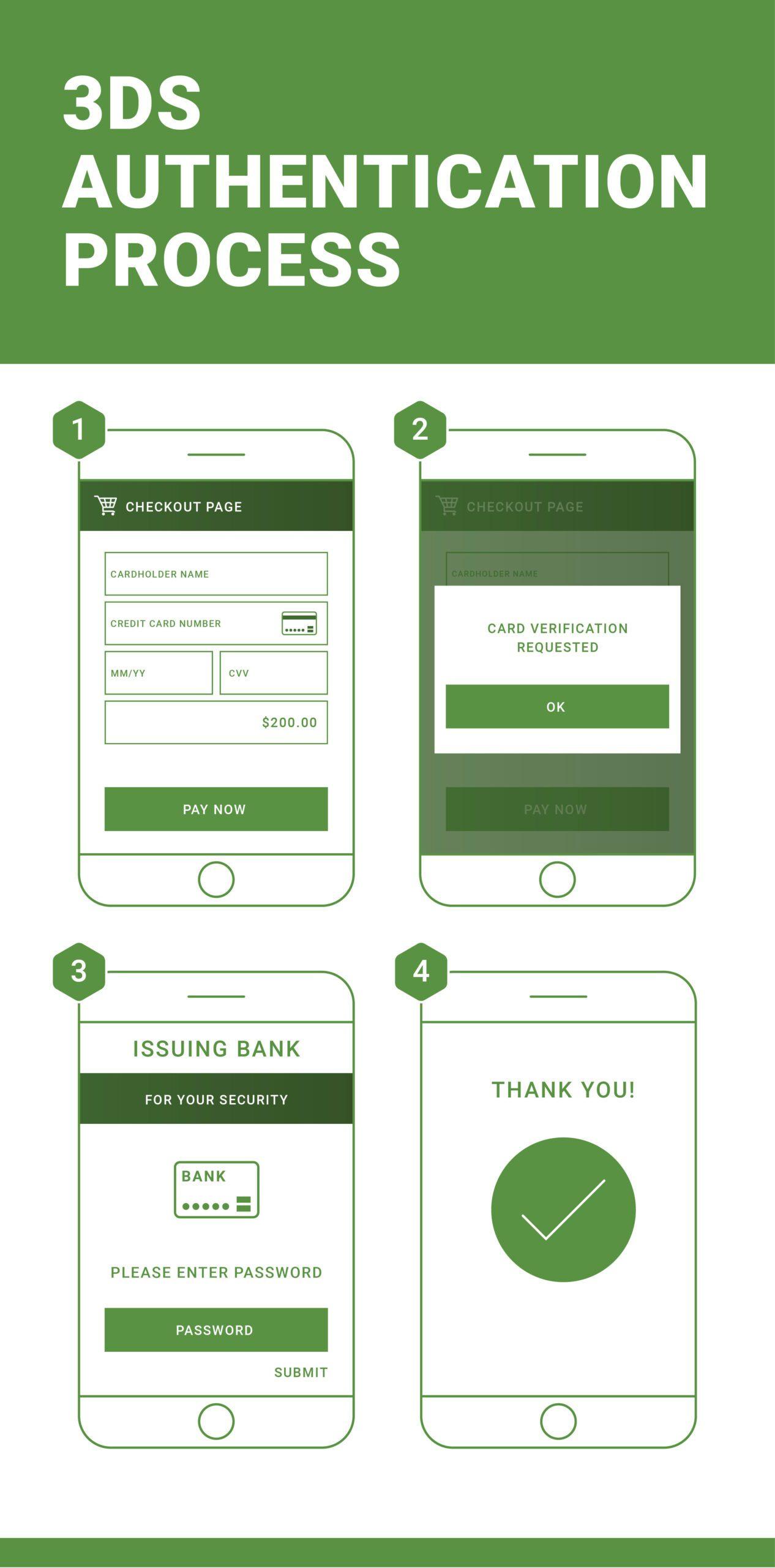
Introduced in 2015, the latest version of this protocol promotes a less intrusive authentication process to reduce the cart abandonment that was occurring during the original 3DS–when users were redirected to the issuing bank’s website to authenticate transactions.
Now, merchants are required to send authentication data along with payment card information to verify the authenticity of the transaction. This process occurs invisibly to the user and authenticates the payment–unless the issuer finds reason to question the legitimacy of the transaction.
If suspicious behavior or an unknown device causes the transaction to be flagged, the user can now receive a text message or confirmation code via an app to verify his or her identity–rather than being redirected to a bank’s website to enter the password associated with the card. The result is a much less disruptive experience for the user.
Integration of 3-D Secure and Other Strong Customer Authentication Protocols
According to Article 97(1) of PSD2, SCA is required in instances where a customer “accesses its payment account online,” “initiates an electronic payment transaction,” or “carries out any action through a remote channel which may imply a risk of payment fraud or other abuses.” This includes nearly all forms of ecommerce, which means SCA is required for many entities doing business in the EU and European Economic Area (EEA). So if you have an ecommerce presence in the EU, you likely will need 3DS or similar authentication technology.
Because 3DS is often used to satisfy this compliance obligation, it’s essential for providers to support 3DS and other SCA techniques. The TokenEx Cloud Security Platform offers a 3-D Secure solution and can integrate with virtually any third-party or API endpoint for maximum flexibility and compliance. Learn more about our payment solutions and flexible integrations by contacting us.
Data Protection for GDPR Compliance
Make sure you’re asking the right questions by reading our ebook now.